Day 29: File Protection Mechanisms
Table of Contents
- Introduction to File Protection Mechanisms
- Understanding Access Control
- Types of File Protection Mechanisms
- 3.1 Permissions (User, Group, Others)
- 3.2 Access Control Lists (ACLs)
- 3.3 Capabilities
- Implementing File Protection in C
- Conclusion
- References
1. Introduction to File Protection Mechanisms
File protection mechanisms are essential for ensuring the security and integrity of files in a computing system. These mechanisms control who can access a file and what operations they can perform on it. In Unix-like operating systems, file protection is typically managed through permissions, access control lists (ACLs), and capabilities. This blog post will delve into the details of these mechanisms, focusing on the low-level aspects of how they work.
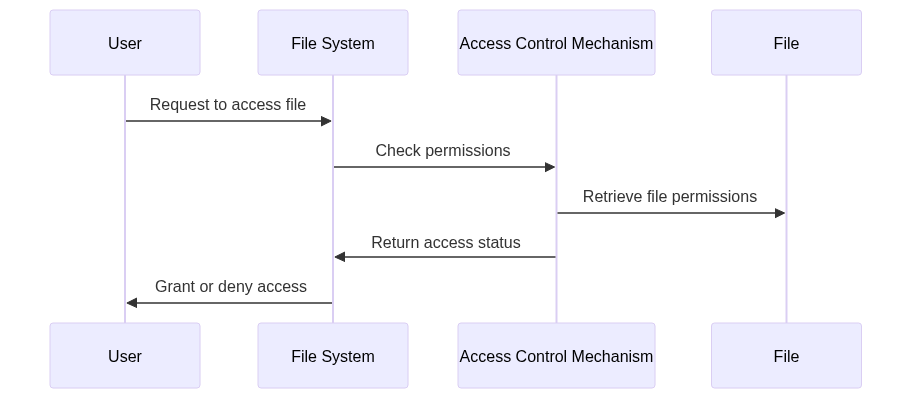
2. Understanding Access Control
Access control is the process of granting or denying access to resources. In the context of file systems, access control determines whether a user or process can read, write, or execute a file. The primary goal of access control is to prevent unauthorized access to files, thereby protecting the data they contain.
3. Types of File Protection Mechanisms
3.1 Permissions (User, Group, Others)
In Unix-like systems, each file is associated with a user and a group. Permissions are set for three categories: the user (owner), the group, and others (everyone else). Each category can have read (r), write (w), and execute (x) permissions.
- User (Owner): The user who owns the file can set permissions for themselves.
- Group: The group associated with the file can have permissions set for all members of the group.
- Others: Everyone else on the system can have permissions set for them.
Explanation:
- Read (r): Allows the file to be read.
- Write (w): Allows the file to be modified.
- Execute (x): Allows the file to be executed (for programs) or allows traversal (for directories).
Example:
-rw-r--r-- 1 user group 0 Jan 1 12:00 file.txt
- The owner (user) has read and write permissions.
- The group has read permissions.
- Others have read permissions.
3.2 Access Control Lists (ACLs)
ACLs provide a more fine-grained access control mechanism than traditional permissions. They allow specific users and groups to be granted or denied access to a file, beyond the basic user, group, and others categories.
Explanation:
- ACL Entries: Each ACL entry specifies a user or group and the permissions granted to them.
- Types of ACLs:
- discretionary access control (DAC): Access is controlled by the file owner.
- mandatory access control (MAC): Access is controlled by the system based on policies.
Example:
setfacl -m u:jane:rwx file.txt
This command grants jane read, write, and execute permissions on file.txt.
3.3 Capabilities
Capabilities are a form of privilege management that allows processes to have specific rights without running as root. They provide a more secure alternative to running processes with elevated privileges.
Explanation:
- Capability-Based Security: Each capability represents a specific privilege, such as the ability to bind to a privileged port or access a device.
- Process Capabilities: Processes can have capabilities assigned to them, which they can use to perform privileged operations.
Example:
cap_set_proc()
This function sets the capabilities of the current process.
4. Implementing File Protection in C
Here is a simple C program that sets file permissions using chmod():
#include <stdio.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <unistd.h>
int main() {
const char *filename = "example.txt";
mode_t mode = S_IRUSR | S_IWUSR | S_IRGRP | S_IROTH; // rw-r--r--
// Create an empty file
creat(filename, mode);
// Set file permissions
if (chmod(filename, mode) == -1) {
perror("chmod");
return 1;
}
printf("File permissions set to %o\n", mode);
return 0;
}
Explanation:
- S_IRUSR: Read permission for the user.
- S_IWUSR: Write permission for the user.
- S_IRGRP: Read permission for the group.
- S_IROTH: Read permission for others.
5. Conclusion
File protection mechanisms are crucial for maintaining the security of files in a system. By understanding and implementing these mechanisms, developers can ensure that their applications handle file access securely.