Day 55: Advanced Microkernel Architecture and Implementation
Table of Content
- Introduction
- Microkernel Core Design
- IPC Mechanisms
- Server Implementation
- Memory Management
- Process Management
- Device Driver Framework
- Security Model
- Performance Optimization
- Conclusion
1. Introduction
Microkernel architecture is a design philosophy that emphasizes minimalism in the kernel, pushing most operating system services into user space. This approach contrasts with monolithic kernels, where the entire operating system runs in kernel space. By reducing the kernel’s responsibilities, microkernels aim to improve system reliability, security, and modularity. This article explains advanced techniques for implementing a microkernel, covering core design, inter-process communication (IPC), server implementation, memory management, and more.
The microkernel design is particularly advantageous in systems where security and fault isolation are critical. By running services like file systems, device drivers, and network stacks in user space, a microkernel can isolate failures, preventing them from crashing the entire system. This modularity also makes it easier to update or replace individual components without affecting the entire operating system. However, this design comes with challenges, particularly in terms of performance, as IPC between user-space services can introduce overhead.
2. Microkernel Core Design
The core of a microkernel is responsible for managing the most fundamental aspects of the system, such as address spaces, threads, and IPC. The provided code defines a microkernel structure that encapsulates these responsibilities. The structure includes fields for address space management, IPC, thread management, capability management, and scheduling. Each of these components is initialized during the microkernel’s startup process.
// Core microkernel structure
struct microkernel {
// Address space management
struct address_space_manager as_mgr;
// IPC subsystem
struct ipc_system ipc;
// Thread management
struct thread_manager thread_mgr;
// Capability management
struct capability_manager cap_mgr;
// Scheduling
struct scheduler sched;
// System state
atomic_t state;
spinlock_t kernel_lock;
};
// Microkernel initialization
int init_microkernel(void) {
struct microkernel* kernel = &g_microkernel;
int ret;
// Initialize core structures
spin_lock_init(&kernel->kernel_lock);
atomic_set(&kernel->state, KERNEL_INITIALIZING);
// Initialize address space management
ret = init_address_space_manager(&kernel->as_mgr);
if (ret)
return ret;
// Initialize IPC system
ret = init_ipc_system(&kernel->ipc);
if (ret)
goto err_ipc;
// Initialize thread management
ret = init_thread_manager(&kernel->thread_mgr);
if (ret)
goto err_thread;
// Initialize capability system
ret = init_capability_manager(&kernel->cap_mgr);
if (ret)
goto err_cap;
// Initialize scheduler
ret = init_scheduler(&kernel->sched);
if (ret)
goto err_sched;
atomic_set(&kernel->state, KERNEL_RUNNING);
return 0;
err_sched:
cleanup_capability_manager(&kernel->cap_mgr);
err_cap:
cleanup_thread_manager(&kernel->thread_mgr);
err_thread:
cleanup_ipc_system(&kernel->ipc);
err_ipc:
cleanup_address_space_manager(&kernel->as_mgr);
return ret;
}
The init_microkernel function initializes these components in a specific order. First, it sets up the address space manager, which is responsible for managing virtual memory. Next, it initializes the IPC system, which handles communication between processes. The thread manager is then initialized to manage threads, followed by the capability manager, which handles access control. Finally, the scheduler is initialized to manage CPU time allocation. If any of these initializations fail, the function cleans up previously initialized components and returns an error code. This careful initialization sequence ensures that the microkernel is in a consistent state before it starts running.
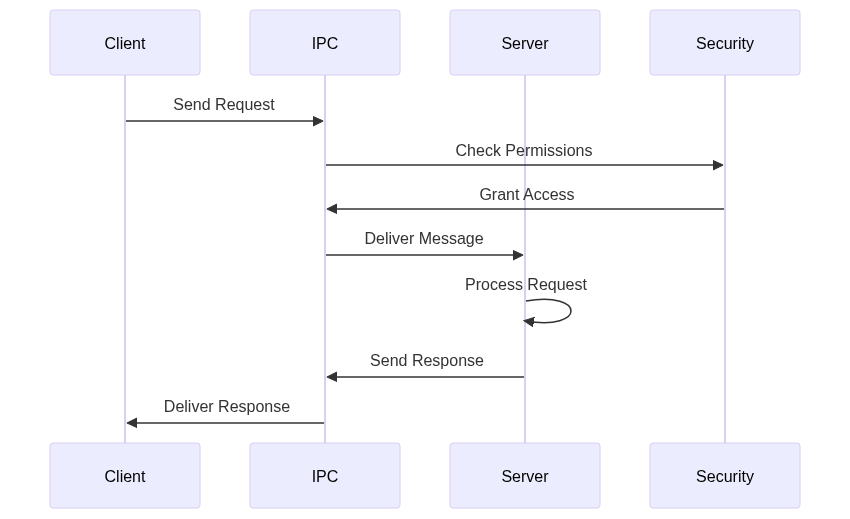
3. IPC Mechanisms
Inter-process communication (IPC) is a cornerstone of microkernel design, as it enables user-space services to communicate with each other. The provided code defines an ipc_message structure that represents a message sent between processes. This structure includes fields for the sender and receiver capabilities, message type, size, and data. The ipc_system structure manages message queues and ports, which are used to route messages between processes.
// IPC message structure
struct ipc_message {
capability_t sender;
capability_t receiver;
uint32_t type;
size_t size;
void* data;
struct list_head list;
};
// IPC system structure
struct ipc_system {
// Message queues
struct list_head msg_queues;
// Port management
struct port_manager ports;
// Synchronization
spinlock_t lock;
struct wait_queue waiters;
};
// Send message implementation
int send_message(capability_t dest, void* data, size_t size) {
struct ipc_message* msg;
struct ipc_system* ipc = &g_microkernel.ipc;
int ret;
// Allocate message structure
msg = kmalloc(sizeof(*msg));
if (!msg)
return -ENOMEM;
// Set up message
msg->sender = get_current_capability();
msg->receiver = dest;
msg->size = size;
msg->data = data;
spin_lock(&ipc->lock);
// Find destination port
struct port* port = find_port(dest);
if (!port) {
ret = -EINVAL;
goto err_port;
}
// Queue message
list_add_tail(&msg->list, &port->message_queue);
// Wake up waiting receiver
wake_up_process(port->waiting_thread);
spin_unlock(&ipc->lock);
return 0;
err_port:
spin_unlock(&ipc->lock);
kfree(msg);
return ret;
}
The send_message function demonstrates how messages are sent in a microkernel. First, it allocates memory for the message and sets up its fields. It then locks the IPC system to prevent concurrent modifications and finds the destination port. If the port exists, the message is added to the port’s message queue, and the receiving thread is woken up to process the message. If the port does not exist, the function returns an error. This mechanism ensures that messages are delivered reliably and efficiently, even in a highly concurrent environment.
4. Server Implementation
In a microkernel, most operating system services are implemented as user-space servers. The provided code defines a server structure that represents such a server. This structure includes fields for server identification, service operations, resource management, client management, and server state. The service_ops structure defines the interface that a server must implement, including functions for initialization, cleanup, request handling, and fault handling.
// Server structure
struct server {
// Server identification
capability_t server_cap;
const char* name;
// Service interface
struct service_ops* ops;
// Resource management
struct resource_manager resources;
// Client management
struct client_manager clients;
// Server state
atomic_t state;
spinlock_t lock;
};
// Service operations interface
struct service_ops {
int (*init)(struct server*);
void (*cleanup)(struct server*);
int (*handle_request)(struct server*, struct ipc_message*);
int (*handle_fault)(struct server*, struct fault_message*);
};
// Server initialization
int init_server(struct server* server, const char* name,
struct service_ops* ops) {
int ret;
server->name = name;
server->ops = ops;
atomic_set(&server->state, SERVER_INITIALIZING);
// Initialize resource management
ret = init_resource_manager(&server->resources);
if (ret)
return ret;
// Initialize client management
ret = init_client_manager(&server->clients);
if (ret)
goto err_client;
// Get server capability
server->server_cap = create_server_capability(server);
if (!is_valid_capability(server->server_cap)) {
ret = -EINVAL;
goto err_cap;
}
// Call service-specific initialization
if (server->ops->init) {
ret = server->ops->init(server);
if (ret)
goto err_init;
}
atomic_set(&server->state, SERVER_RUNNING);
return 0;
err_init:
destroy_server_capability(server->server_cap);
err_cap:
cleanup_client_manager(&server->clients);
err_client:
cleanup_resource_manager(&server->resources);
return ret;
}
The init_server function initializes a server by setting up its resource and client management systems. It then creates a capability for the server, which is used to identify and access the server. Finally, it calls the server’s initialization function, if one is provided. If any of these steps fail, the function cleans up previously initialized components and returns an error. This initialization process ensures that the server is ready to handle requests from clients.
5. Memory Management
Memory management in a microkernel involves managing virtual address spaces and memory regions. The provided code defines a memory_region structure that represents a region of virtual memory. This structure includes fields for the region’s start address, size, and flags. The address_space structure represents a process’s virtual address space, including its page directory, memory regions, and reference count.
// Memory region structure
struct memory_region {
void* start;
size_t size;
uint32_t flags;
struct list_head list;
};
// Address space structure
struct address_space {
// Page directory
void* pgd;
// Memory regions
struct list_head regions;
// Reference counting
atomic_t ref_count;
// Lock for modifications
spinlock_t lock;
};
// Map memory region
int map_memory_region(struct address_space* as,
void* vaddr, size_t size,
uint32_t flags) {
struct memory_region* region;
unsigned long irq_flags;
int ret;
// Allocate region descriptor
region = kmalloc(sizeof(*region));
if (!region)
return -ENOMEM;
region->start = vaddr;
region->size = size;
region->flags = flags;
spin_lock_irqsave(&as->lock, irq_flags);
// Check for overlapping regions
if (check_overlap(as, vaddr, size)) {
ret = -EEXIST;
goto err_overlap;
}
// Perform actual mapping
ret = do_map_pages(as->pgd, vaddr, size, flags);
if (ret)
goto err_map;
// Add to region list
list_add(®ion->list, &as->regions);
spin_unlock_irqrestore(&as->lock, irq_flags);
return 0;
err_map:
err_overlap:
spin_unlock_irqrestore(&as->lock, irq_flags);
kfree(region);
return ret;
}
The map_memory_region function demonstrates how memory regions are mapped into an address space. First, it allocates a memory_region structure and sets up its fields. It then locks the address space to prevent concurrent modifications and checks for overlapping regions. If no overlaps are found, it maps the pages into the address space and adds the region to the region list. If any of these steps fail, the function cleans up and returns an error. This mechanism ensures that memory is allocated and mapped correctly, preventing conflicts and ensuring security.
6. Process Management
Process management in a microkernel involves creating and managing processes, which are the basic units of execution. The provided code defines a process structure that represents a process. This structure includes fields for process identification, address space, thread management, capability space, resource accounting, and process state.
// Process structure
struct process {
// Process identification
pid_t pid;
capability_t process_cap;
// Address space
struct address_space* as;
// Thread management
struct list_head threads;
// Capability space
struct capability_space* cap_space;
// Resource accounting
struct resource_usage usage;
// Process state
atomic_t state;
spinlock_t lock;
};
// Create new process
struct process* create_process(void) {
struct process* proc;
int ret;
// Allocate process structure
proc = kmalloc(sizeof(*proc));
if (!proc)
return ERR_PTR(-ENOMEM);
// Initialize basic fields
proc->pid = allocate_pid();
atomic_set(&proc->state, PROCESS_INITIALIZING);
spin_lock_init(&proc->lock);
INIT_LIST_HEAD(&proc->threads);
// Create address space
proc->as = create_address_space();
if (IS_ERR(proc->as)) {
ret = PTR_ERR(proc->as);
goto err_as;
}
// Create capability space
proc->cap_space = create_capability_space();
if (IS_ERR(proc->cap_space)) {
ret = PTR_ERR(proc->cap_space);
goto err_cap;
}
// Create process capability
proc->process_cap = create_process_capability(proc);
if (!is_valid_capability(proc->process_cap)) {
ret = -EINVAL;
goto err_proc_cap;
}
atomic_set(&proc->state, PROCESS_RUNNING);
return proc;
err_proc_cap:
destroy_capability_space(proc->cap_space);
err_cap:
destroy_address_space(proc->as);
err_as:
free_pid(proc->pid);
kfree(proc);
return ERR_PTR(ret);
}
The create_process function demonstrates how processes are created. First, it allocates memory for the process structure and initializes its fields. It then creates an address space and capability space for the process. Finally, it creates a capability for the process, which is used to identify and access the process. If any of these steps fail, the function cleans up and returns an error. This process creation mechanism ensures that each process has its own isolated address space and capability space, providing security and fault isolation.
7. Device Driver Framework
Device drivers in a microkernel are typically implemented as user-space servers. The provided code defines a device_server structure that represents such a server. This structure includes fields for the base server, driver operations, device, interrupt management, and DMA management.
// Device driver interface
struct driver_ops {
int (*probe)(struct device*);
void (*remove)(struct device*);
int (*suspend)(struct device*);
int (*resume)(struct device*);
int (*handle_interrupt)(struct device*);
};
// Device server structure
struct device_server {
struct server base;
struct driver_ops* ops;
struct device* dev;
// Interrupt management
int irq;
struct interrupt_handler int_handler;
// DMA management
struct dma_manager dma;
};
// Initialize device server
int init_device_server(struct device_server* server,
const char* name,
struct driver_ops* ops) {
int ret;
// Initialize base server
ret = init_server(&server->base, name, &device_service_ops);
if (ret)
return ret;
server->ops = ops;
// Initialize DMA management
ret = init_dma_manager(&server->dma);
if (ret)
goto err_dma;
// Probe device
if (server->ops->probe) {
ret = server->ops->probe(server->dev);
if (ret)
goto err_probe;
}
return 0;
err_probe:
cleanup_dma_manager(&server->dma);
err_dma:
cleanup_server(&server->base);
return ret;
}
The init_device_server function initializes a device server by setting up its base server and DMA management. It then probes the device using the driver’s probe function. If the probe is successful, the server is ready to handle requests from clients. If any of these steps fail, the function cleans up and returns an error. This initialization process ensures that the device server is ready to manage its device and handle interrupts.
8. Security Model
Security in a microkernel is typically implemented using a capability-based access control system. The provided code defines a security_context structure that represents a security context. This structure includes fields for capability sets, access control lists, security policies, and audit logs.
// Security context structure
struct security_context {
// Capability set
struct capability_set caps;
// Access control
struct access_control_list acl;
// Security policy
struct security_policy* policy;
// Audit trail
struct audit_log* audit;
};
// Security policy interface
struct security_policy {
int (*check_access)(struct security_context*, capability_t, uint32_t);
int (*grant_capability)(struct security_context*, capability_t);
int (*revoke_capability)(struct security_context*, capability_t);
void (*audit_event)(struct security_context*, struct audit_event*);
};
// Check access permission
int check_security_access(struct security_context* ctx,
capability_t target,
uint32_t requested_rights) {
int ret;
// Check capability possession
if (!has_capability(ctx, target))
return -EPERM;
// Check access rights
ret = ctx->policy->check_access(ctx, target, requested_rights);
if (ret)
return ret;
// Log access attempt
audit_access_attempt(ctx, target, requested_rights);
return 0;
}
The check_security_access function demonstrates how access permissions are checked. First, it checks if the security context possesses the required capability. It then checks if the requested access rights are allowed by the security policy. If both checks pass, the function logs the access attempt and returns success. If either check fails, the function returns an error. This mechanism ensures that only authorized processes can access resources, providing fine-grained security.
9. Performance Optimization
Performance optimization in a microkernel often involves optimizing IPC, as it is a critical path for system performance. The provided code defines a fast_path_ipc function that demonstrates a fast path for IPC. This function checks if the destination is eligible for the fast path and, if so, directly copies the message to the target thread’s buffer. If the destination is not eligible, it falls back to the slow path. This optimization reduces overhead for frequently used IPC paths, improving overall system performance.
// Fast path IPC
int fast_path_ipc(capability_t dest, void* data, size_t size) {
struct thread* current = get_current_thread();
struct thread* target;
// Check fast path conditions
if (!is_fast_path_eligible(dest))
return slow_path_ipc(dest, data, size);
// Get target thread
target = capability_to_thread(dest);
if (!target)
return -EINVAL;
// Direct message copy
if (size <= FAST_PATH_SIZE) {
memcpy(target->ipc_buffer, data, size);
target->ipc_size = size;
// Wake up target
wake_up_process(target);
return 0;
}
return slow_path_ipc(dest, data, size);
}
// IPC path optimization
struct ipc_path {
// Cache of frequently used paths
struct {
capability_t dest;
struct thread* target;
uint32_t flags;
} cache[IPC_CACHE_SIZE];
// Statistics
atomic_t hits;
atomic_t misses;
};
// Initialize IPC path optimization
void init_ipc_path(struct ipc_path* path) {
memset(path->cache, 0, sizeof(path->cache));
atomic_set(&path->hits, 0);
atomic_set(&path->misses, 0);
}
The ipc_path structure is used to cache frequently used IPC paths, reducing the need for repeated lookups. The init_ipc_path function initializes this cache, setting up the data structures needed for tracking hits and misses. This caching mechanism further optimizes IPC performance by reducing the overhead of path resolution.
10. Conclusion
Advanced microkernel design requires careful consideration of IPC mechanisms, security models, and performance optimization. This article has covered the essential components needed to build a modern microkernel-based operating system, including core design, IPC, server implementation, memory management, process management, device driver frameworks, and security models. Each component plays a critical role in ensuring the system’s reliability, security, and performance.
Key takeaways include the importance of IPC optimization for microkernel performance, the need to build security into the core design, and the benefits of capability-based access control. The modularity provided by server-based design makes it easier to maintain and update the system, while performance optimization techniques ensure that the system can handle high loads efficiently.