Day 61: Security Vulnerability Analysis - Focus on Buffer Overflow
1. Introduction
Buffer overflow vulnerabilities remain one of the most critical security issues in system programming. This comprehensive guide explores the technical details of buffer overflow attacks, detection methods, and prevention strategies. Buffer overflows occur when a program writes more data to a buffer than it can hold, potentially overwriting adjacent memory and leading to arbitrary code execution, crashes, or other unintended behavior.
Understanding buffer overflow vulnerabilities is essential for developing secure software. By implementing proper detection and prevention techniques, developers can protect their applications from exploitation and ensure the integrity of their systems.
2. Buffer Overflow Fundamentals
2.1 Basic Buffer Overflow Example
A buffer overflow occurs when data is written beyond the bounds of a buffer, potentially overwriting adjacent memory. This can lead to various security issues, including arbitrary code execution and system crashes.
Here’s an example of a vulnerable function that demonstrates a stack buffer overflow:
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
// Vulnerable function demonstrating stack buffer overflow
void vulnerable_function(char *input) {
char buffer[64];
strcpy(buffer, input); // Vulnerable - no bounds checking
printf("Buffer contains: %s\n", buffer);
}
// Secure version with bounds checking
void secure_function(char *input) {
char buffer[64];
size_t input_len = strlen(input);
if (input_len >= sizeof(buffer)) {
fprintf(stderr, "Input too long - would cause buffer overflow\n");
return;
}
strncpy(buffer, input, sizeof(buffer) - 1);
buffer[sizeof(buffer) - 1] = '\0';
printf("Buffer contains: %s\n", buffer);
}
// Memory corruption detection
void memory_guard_example(void) {
char *guard_page = mmap(NULL, 4096,
PROT_READ | PROT_WRITE,
MAP_PRIVATE | MAP_ANONYMOUS,
-1, 0);
if (guard_page == MAP_FAILED) {
perror("mmap failed");
return;
}
// Protect the page
if (mprotect(guard_page, 4096, PROT_NONE) == -1) {
perror("mprotect failed");
munmap(guard_page, 4096);
return;
}
}
In this example, the vulnerable_function is susceptible to a buffer overflow because it uses strcpy without bounds checking. The secure_function demonstrates how to prevent buffer overflows by using strncpy and checking the input length. The memory_guard_example function shows how to use memory protection to detect memory corruption.
2.2 Advanced Buffer Overflow Detection
Advanced techniques for detecting buffer overflows include using canaries, Address Space Layout Randomization (ASLR), and stack protection.
Here’s an example of a canary implementation for detecting buffer overflows:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <signal.h>
#include <unistd.h>
#include <sys/mman.h>
// Canary implementation
typedef struct {
unsigned long canary;
void *buffer;
size_t size;
} protected_buffer_t;
#define CANARY_VALUE 0xDEADBEEF
protected_buffer_t *create_protected_buffer(size_t size) {
protected_buffer_t *pb = malloc(sizeof(protected_buffer_t));
if (!pb) return NULL;
pb->buffer = malloc(size);
if (!pb->buffer) {
free(pb);
return NULL;
}
pb->canary = CANARY_VALUE;
pb->size = size;
return pb;
}
int check_buffer_integrity(protected_buffer_t *pb) {
if (pb->canary != CANARY_VALUE) {
fprintf(stderr, "Buffer overflow detected! Canary corrupted!\n");
return -1;
}
return 0;
}
// ASLR demonstration
void demonstrate_aslr(void) {
void *ptr1 = malloc(100);
void *ptr2 = malloc(100);
printf("Address 1: %p\n", ptr1);
printf("Address 2: %p\n", ptr2);
free(ptr1);
free(ptr2);
}
// Stack protection with compiler flags
// Compile with: gcc -fstack-protector-all
void stack_protection_example(char *input) {
char protected_buffer[64];
// GCC will automatically add stack canaries
strncpy(protected_buffer, input, sizeof(protected_buffer) - 1);
}
// Heap overflow detection
typedef struct {
size_t size;
unsigned char *data;
unsigned long checksum;
} heap_protected_block_t;
unsigned long calculate_checksum(unsigned char *data, size_t size) {
unsigned long sum = 0;
for (size_t i = 0; i < size; i++) {
sum += data[i];
}
return sum;
}
heap_protected_block_t *create_protected_heap_block(size_t size) {
heap_protected_block_t *block = malloc(sizeof(heap_protected_block_t));
if (!block) return NULL;
block->data = malloc(size);
if (!block->data) {
free(block);
return NULL;
}
block->size = size;
memset(block->data, 0, size);
block->checksum = calculate_checksum(block->data, size);
return block;
}
int verify_heap_block(heap_protected_block_t *block) {
unsigned long current_checksum = calculate_checksum(block->data,
block->size);
if (current_checksum != block->checksum) {
fprintf(stderr, "Heap corruption detected!\n");
return -1;
}
return 0;
}
In this example, the protected_buffer_t structure includes a canary value that is checked for integrity. The demonstrate_aslr function shows how ASLR randomizes memory addresses to make exploitation more difficult. The stack_protection_example function demonstrates how to use compiler flags to enable stack protection. The heap_protected_block_t structure includes a checksum to detect heap corruption.
3. Exploitation Prevention System
Preventing buffer overflow exploitation involves using techniques such as Data Execution Prevention (DEP), format string vulnerability prevention, and memory sanitization.
Here’s an example of implementing DEP and preventing format string vulnerabilities:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/mman.h>
#include <unistd.h>
// DEP (Data Execution Prevention) implementation
void implement_dep(void) {
// Allocate non-executable memory
void *memory = mmap(NULL, 4096,
PROT_READ | PROT_WRITE,
MAP_PRIVATE | MAP_ANONYMOUS,
-1, 0);
if (memory == MAP_FAILED) {
perror("mmap failed");
return;
}
// Make memory non-executable
if (mprotect(memory, 4096, PROT_READ | PROT_WRITE) == -1) {
perror("mprotect failed");
munmap(memory, 4096);
return;
}
}
// Format string vulnerability prevention
void secure_printf(const char *format, ...) {
// Verify format string doesn't contain %n
if (strchr(format, '%n') != NULL) {
fprintf(stderr, "Format string attack detected!\n");
return;
}
va_list args;
va_start(args, format);
vprintf(format, args);
va_end(args);
}
// Memory sanitization
void secure_memory_clear(void *ptr, size_t size) {
volatile unsigned char *p = ptr;
while (size--) {
*p++ = 0;
}
}
In this example, the implement_dep function demonstrates how to allocate non-executable memory using mmap and mprotect. The secure_printf function prevents format string vulnerabilities by checking for the %n format specifier. The secure_memory_clear function securely clears memory to prevent data leakage.
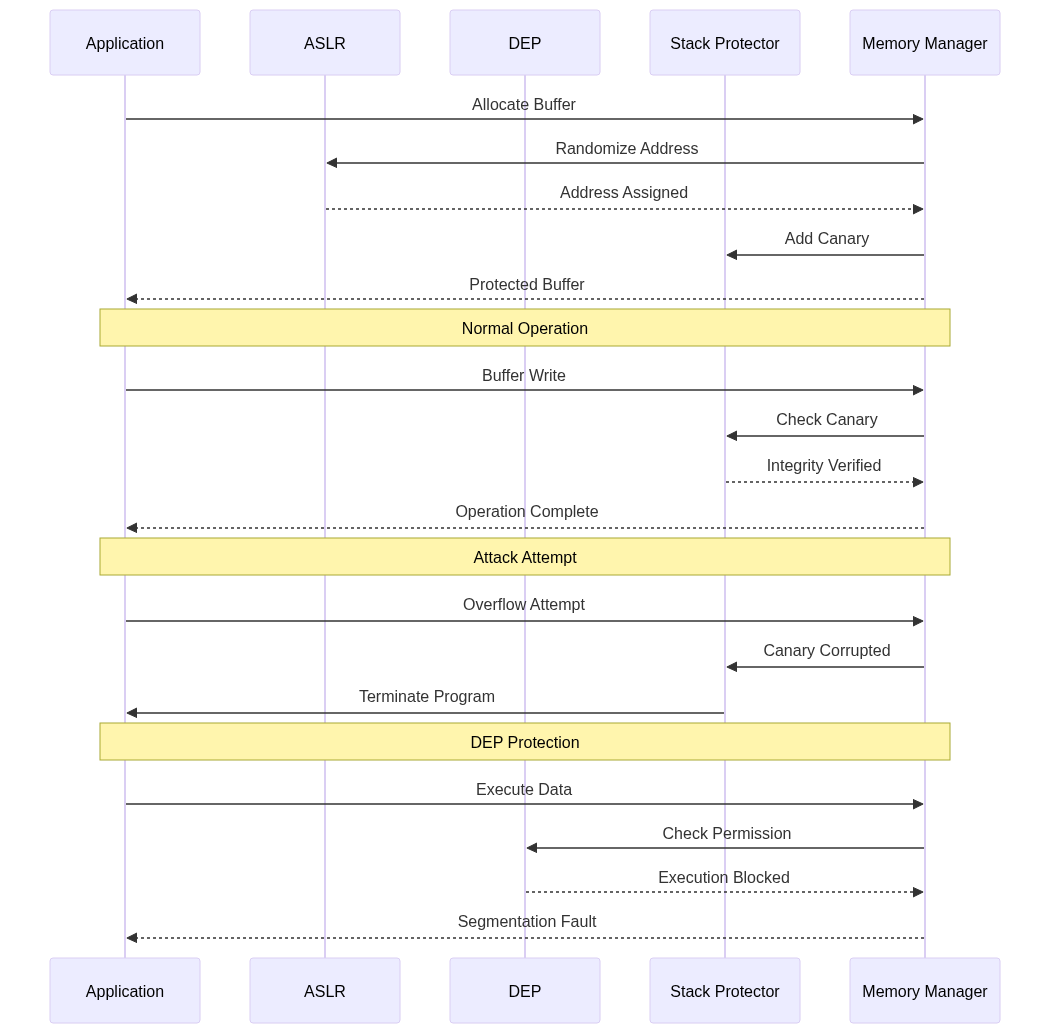
4. System Architecture
The system architecture for preventing buffer overflow exploitation typically involves several components, including ASLR, DEP, stack protection, and memory management. These components work together to detect and prevent buffer overflow attacks.
In this architecture, the application allocates a buffer, and the memory manager randomizes the address using ASLR. The stack protector adds a canary to detect buffer overflows. If an overflow attempt is detected, the program is terminated. DEP prevents the execution of data in non-executable memory, blocking exploitation attempts.
5. Detection and Prevention Tools
5.1 Static Analysis Tool
Static analysis tools can help detect potential buffer overflow vulnerabilities in source code. Here’s an example of a simple static analysis tool in Python:
import re
import ast
def analyze_c_file(filename):
vulnerabilities = []
with open(filename, 'r') as file:
content = file.read()
# Check for unsafe functions
unsafe_functions = {
'strcpy': 'Use strncpy instead',
'gets': 'Use fgets instead',
'sprintf': 'Use snprintf instead'
}
for func, recommendation in unsafe_functions.items():
matches = re.finditer(r'\b' + func + r'\s*\(', content)
for match in matches:
vulnerabilities.append({
'type': 'Unsafe Function',
'function': func,
'line': content[:match.start()].count('\n') + 1,
'recommendation': recommendation
})
# Check for buffer size declarations
buffer_decls = re.finditer(
r'char\s+(\w+)\s*\[(\d+)\]', content
)
for match in buffer_decls:
buffer_name = match.group(1)
buffer_size = int(match.group(2))
# Check for potential overflow in nearby strcpy calls
strcpy_check = re.search(
r'strcpy\s*\(\s*' + buffer_name + r'\s*,',
content
)
if strcpy_check:
vulnerabilities.append({
'type': 'Potential Buffer Overflow',
'buffer': buffer_name,
'size': buffer_size,
'line': content[:strcpy_check.start()].count('\n') + 1
})
return vulnerabilities
This static analysis tool checks for unsafe functions like strcpy, gets, and sprintf, and identifies potential buffer overflow vulnerabilities by analyzing buffer size declarations and nearby strcpy calls.
6. Best Practices
Key security considerations:
-
Input Validation: Always validate input length and content before processing. Implement strict bounds checking and input sanitization to prevent buffer overflow attacks.
-
Memory Management: Use secure memory allocation and deallocation practices. Implement proper memory alignment and padding to prevent overflow between adjacent buffers.
-
Compiler Protections: Enable and properly configure compiler security features such as stack protection, ASLR, and DEP. Regular security audits and testing should be performed.
By following these best practices, developers can significantly reduce the risk of buffer overflow vulnerabilities in their applications.
7. Conclusion
Buffer overflow vulnerabilities remain a significant security concern in system programming. Understanding the mechanisms of these vulnerabilities and implementing proper prevention techniques is crucial for developing secure systems. By leveraging techniques such as input validation, memory management, and compiler protections, developers can protect their applications from exploitation and ensure the integrity of their systems.