Day 63: Kernel-Level Malware Detection in Modern Operating Systems
Table of Contents
- Introduction
- Kernel-Level Detection Fundamentals
- Detection Mechanisms
- Hooking Techniques
- Memory Analysis
- System Architecture
- Behavioral Analysis
- Testing Framework
- Further Reading
- Conclusion
1. Introduction
Kernel-level malware detection represents one of the most effective approaches to identifying and preventing sophisticated malware attacks. This article explores advanced techniques for implementing malware detection at the kernel level, focusing on real-time monitoring, system call interception, and behavioral analysis.
Malware detection at the kernel level is crucial because it allows for deep visibility into system operations, enabling the detection of malicious activities that might otherwise go unnoticed. By implementing these techniques, developers can create robust security mechanisms that protect systems from a wide range of threats.
2. Kernel-Level Detection Fundamentals
The core principles of kernel-level malware detection include:
-
System Call Monitoring: Kernel-level detection systems intercept and analyze system calls to identify malicious patterns. This involves monitoring process creation, file operations, network connections, and memory modifications. The monitoring system maintains detailed logs of system call parameters and their execution context.
-
Memory Protection: Implementation of memory protection mechanisms to prevent unauthorized code execution and data modification. This includes page table monitoring, memory mapping validation, and protection against code injection attacks. The system implements various memory protection schemes including W^X (Write XOR Execute) and ASLR (Address Space Layout Randomization).
-
Process Tracking: Continuous monitoring of process creation, termination, and behavior patterns. This includes tracking process hierarchies, resource usage, and inter-process communications. The system maintains a process activity database for pattern analysis and anomaly detection.
Understanding these fundamentals is essential for building effective kernel-level malware detection systems. By monitoring system calls, protecting memory, and tracking processes, developers can detect and prevent malicious activities before they cause harm.
3. Detection Mechanisms
Here’s a detailed implementation of various detection mechanisms:
#include <linux/module.h>
#include <linux/kernel.h>
#include <linux/init.h>
#include <linux/syscalls.h>
#include <linux/slab.h>
#include <linux/kprobes.h>
#include <linux/binfmts.h>
#include <linux/fs.h>
struct malware_detector {
struct list_head list;
unsigned long syscall_table;
void **original_syscalls;
struct mutex lock;
atomic_t active_scans;
};
static struct malware_detector *detector;
struct syscall_info {
unsigned long syscall_nr;
unsigned long args[6];
pid_t pid;
uid_t uid;
char comm[TASK_COMM_LEN];
};
static DEFINE_SPINLOCK(detector_lock);
static LIST_HEAD(suspicious_processes);
static asmlinkage long (*original_execve)(const char __user *filename,
const char __user *const __user *argv,
const char __user *const __user *envp);
static asmlinkage long detector_execve(const char __user *filename,
const char __user *const __user *argv,
const char __user *const __user *envp)
{
struct syscall_info *info;
char *kernel_filename;
int ret;
info = kmalloc(sizeof(*info), GFP_KERNEL);
if (!info)
return -ENOMEM;
kernel_filename = kmalloc(PATH_MAX, GFP_KERNEL);
if (!kernel_filename) {
kfree(info);
return -ENOMEM;
}
if (strncpy_from_user(kernel_filename, filename, PATH_MAX) < 0) {
kfree(kernel_filename);
kfree(info);
return -EFAULT;
}
info->syscall_nr = __NR_execve;
info->pid = current->pid;
info->uid = current_uid().val;
memcpy(info->comm, current->comm, TASK_COMM_LEN);
if (analyze_process_behavior(info)) {
spin_lock(&detector_lock);
list_add(&info->list, &suspicious_processes);
spin_unlock(&detector_lock);
}
ret = original_execve(filename, argv, envp);
kfree(kernel_filename);
return ret;
}
static int analyze_process_behavior(struct syscall_info *info)
{
static const char *suspicious_patterns[] = {
"/proc/kcore",
"/dev/mem",
"/dev/kmem",
NULL
};
int i;
char *process_path;
process_path = kmalloc(PATH_MAX, GFP_KERNEL);
if (!process_path)
return 0;
if (get_process_path(info->pid, process_path, PATH_MAX) < 0) {
kfree(process_path);
return 0;
}
for (i = 0; suspicious_patterns[i]; i++) {
if (strstr(process_path, suspicious_patterns[i])) {
kfree(process_path);
return 1;
}
}
kfree(process_path);
return 0;
}
In this example, the detector_execve function intercepts the execve system call and analyzes the process behavior. If the process exhibits suspicious behavior, it is added to a list of suspicious processes for further investigation.
4. Memory Analysis Implementation
Memory analysis is a critical component of kernel-level malware detection. Here’s an example of how to analyze memory regions for suspicious activity:
static int analyze_memory_region(struct mm_struct *mm, unsigned long start,
unsigned long end)
{
struct vm_area_struct *vma;
unsigned long flags;
int suspicious = 0;
vma = find_vma(mm, start);
if (!vma || vma->vm_start > start)
return -EINVAL;
flags = vma->vm_flags;
if ((flags & VM_WRITE) && (flags & VM_EXEC)) {
suspicious = 1;
log_suspicious_memory("W^X violation detected", vma);
}
if (flags & VM_MAYSHARE) {
if (check_shared_memory_integrity(vma) < 0) {
suspicious = 1;
log_suspicious_memory("Suspicious shared memory", vma);
}
}
return suspicious;
}
In this example, the analyze_memory_region function checks for W^X violations and suspicious shared memory regions. If any suspicious activity is detected, it is logged for further analysis.
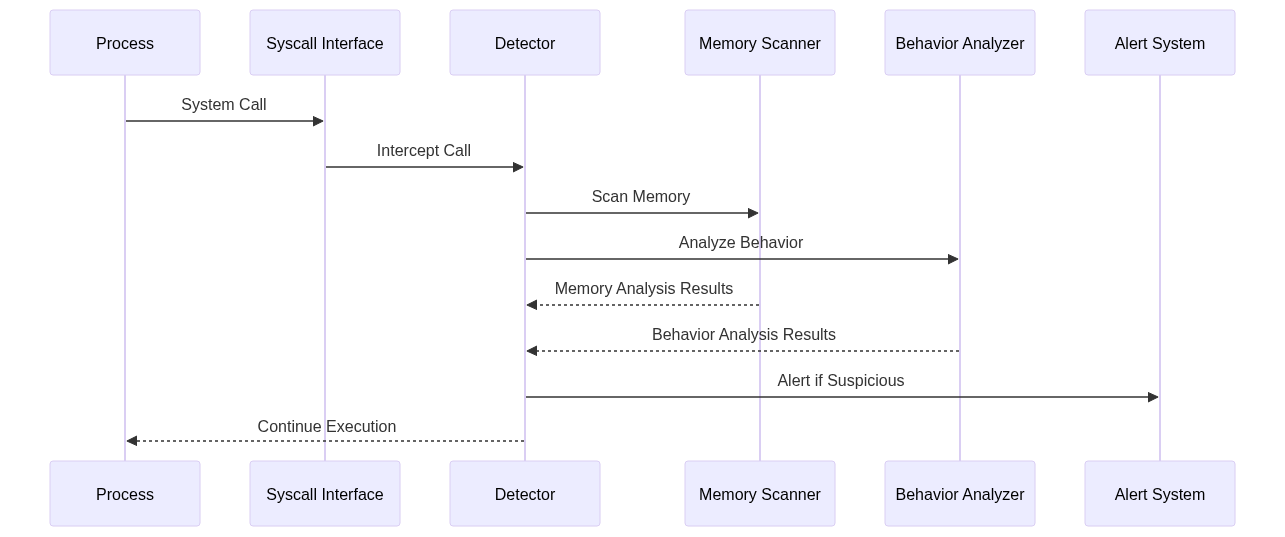
5. System Architecture
The system architecture for kernel-level malware detection involves several components, including the process, system call interface, detector, memory scanner, behavior analyzer, and alert system. These components work together to detect and prevent malicious activities.
In this architecture, the process makes a system call, which is intercepted by the detector. The detector then scans the memory and analyzes the behavior of the process. If any suspicious activity is detected, an alert is generated, and the process continues execution.
6. Behavioral Analysis
Key aspects of behavioral analysis include:
-
System Call Patterns: Analysis of system call sequences and frequencies to identify malicious behavior. The system maintains a database of known malicious patterns and uses machine learning algorithms for pattern matching. Each process’s system call sequence is compared against known malicious patterns.
-
Resource Usage Monitoring: Tracking CPU, memory, and I/O usage patterns to detect anomalous behavior. The system establishes baseline metrics for normal process behavior and flags significant deviations. This includes monitoring for sudden spikes in resource usage or unusual access patterns.
-
Network Activity Analysis: Monitoring network connections and data transfer patterns for suspicious activity. The system tracks connection attempts, data flow patterns, and protocol usage to identify potential command and control communications or data exfiltration attempts.
By analyzing these aspects, developers can detect and prevent malicious activities before they cause harm.
7. Performance Impact Monitoring
Monitoring the performance impact of kernel-level malware detection is crucial for ensuring that the system remains efficient and responsive. Here’s an example of how to track performance metrics:
struct performance_metrics {
unsigned long detection_latency;
unsigned long cpu_usage;
unsigned long memory_overhead;
atomic_t false_positives;
atomic_t true_positives;
};
static struct performance_metrics *metrics;
static void update_performance_metrics(void)
{
unsigned long flags;
struct timespec64 ts;
spin_lock_irqsave(&metrics_lock, flags);
ktime_get_real_ts64(&ts);
metrics->detection_latency = calculate_average_latency();
metrics->cpu_usage = calculate_cpu_usage();
metrics->memory_overhead = calculate_memory_usage();
spin_unlock_irqrestore(&metrics_lock, flags);
}
In this example, the update_performance_metrics function updates various performance metrics, including detection latency, CPU usage, and memory overhead. These metrics are used to ensure that the malware detection system does not negatively impact system performance.
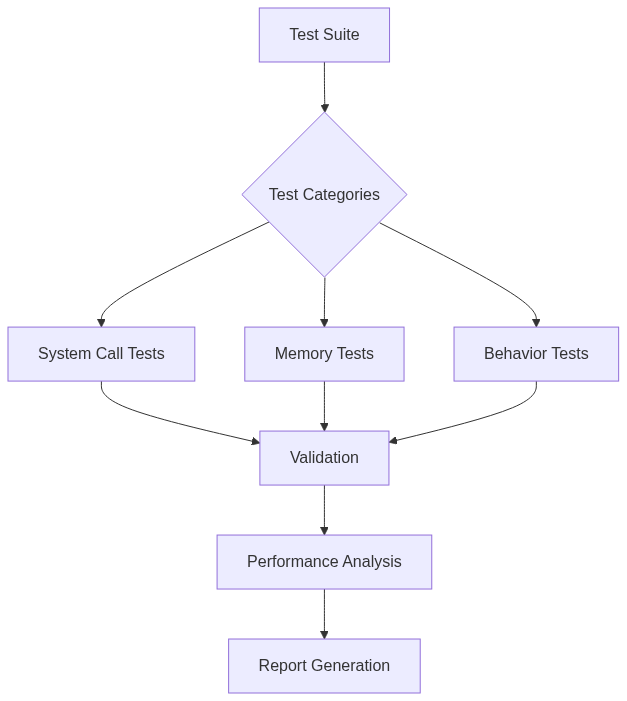
8. Testing Framework
A robust testing framework is essential for validating the effectiveness of kernel-level malware detection systems. Here’s an example of a testing framework:
In this framework, the test suite is divided into categories, including system call tests, memory tests, and behavior tests. The results of these tests are validated, and performance analysis is conducted to generate a comprehensive report.
9. Further Reading
- “Rootkits: Subverting the Windows Kernel” by Greg Hoglund
- “The Art of Memory Forensics” by Michael Hale Ligh
- “Malware Analyst’s Cookbook” by Michael Ligh
- Linux Security Modules Documentation
- “Understanding the Linux Kernel” - Chapter on Security
- Academic Papers on Kernel-Level Malware Detection
These resources provide valuable insights into kernel-level malware detection and can help developers build more robust security mechanisms.
10. Conclusion
Kernel-level malware detection requires a comprehensive approach combining system call monitoring, memory analysis, and behavioral detection. The implementation provided demonstrates practical techniques for building robust detection systems while maintaining system performance.
By leveraging these techniques, developers can create effective malware detection systems that protect systems from a wide range of threats. The provided code examples and architectural patterns serve as a foundation for building production-grade malware detection implementations.