Day 67: From Panic to Resolution: Implementing Kernel Debugging Techniques for Crash Analysis
Introduction
Kernel debugging techniques, particularly crash analysis, are essential for maintaining and troubleshooting operating systems. This article explores the implementation of kernel debugging mechanisms, focusing on crash analysis, stack trace examination, and memory dump investigation. Kernel crashes can occur due to various reasons, such as hardware failures, software bugs, or invalid memory accesses. Debugging these crashes requires a deep understanding of the kernel’s internal state and the ability to capture and analyze critical information.
The implementation discussed here focuses on building a robust kernel debugging system capable of capturing crash dumps, analyzing stack traces, and examining memory regions. By the end of this guide, you will have a solid understanding of how to design and implement kernel debugging tools suitable for diagnosing and resolving complex system issues.
Kernel Debugging Architecture
The architecture of the kernel debugging system is built around several core components. The first is crash dump collection, which involves capturing the system state during a crash. This includes saving the contents of memory, CPU registers, and stack traces. The system must be able to freeze the system state to ensure that the captured information is accurate and consistent.
Another key component is debug information management. This involves handling debug symbols and stack unwinding information, which are essential for interpreting the captured data. The system supports both built-in and loadable module debugging, allowing developers to debug kernel modules as well as the core kernel.
Finally, the system includes live analysis tools, which allow developers to examine the running kernel state. These tools provide mechanisms for setting breakpoints, watchpoints, and inspecting the state of the system in real-time.
Implementation of Kernel Debugger
The implementation begins with defining the kernel_debugger structure, which manages the debugging system. This structure includes a stack trace buffer, a crash dump buffer, and a spinlock for synchronization.
#include <linux/module.h>
#include <linux/kernel.h>
#include <linux/kprobes.h>
#include <linux/kallsyms.h>
#include <linux/slab.h>
#include <linux/stacktrace.h>
#include <linux/kdebug.h>
#include <linux/mm.h>
#define MAX_STACK_TRACE_DEPTH 64
#define MAX_CRASH_DUMP_SIZE (1UL << 20) // 1MB
struct kernel_debugger {
struct kprobe *probes;
unsigned long *stack_trace;
unsigned int trace_size;
spinlock_t debug_lock;
atomic_t active_traces;
void *crash_buffer;
size_t crash_size;
};
struct debug_context {
unsigned long registers[32];
struct pt_regs *regs;
unsigned long ip;
unsigned long sp;
int cpu;
pid_t pid;
char comm[TASK_COMM_LEN];
};
static struct kernel_debugger debugger;
The init_kernel_debugger function initializes the kernel debugger. It allocates memory for the stack trace buffer and crash dump buffer, initializes the spinlock, and sets up the active traces counter.
static int init_kernel_debugger(void)
{
debugger.stack_trace = kmalloc_array(MAX_STACK_TRACE_DEPTH,
sizeof(unsigned long),
GFP_KERNEL);
if (!debugger.stack_trace)
return -ENOMEM;
debugger.crash_buffer = vmalloc(MAX_CRASH_DUMP_SIZE);
if (!debugger.crash_buffer) {
kfree(debugger.stack_trace);
return -ENOMEM;
}
spin_lock_init(&debugger.debug_lock);
atomic_set(&debugger.active_traces, 0);
return 0;
}
The capture_debug_info function captures the current state of the system, including the CPU registers, instruction pointer, stack pointer, and task information.
static void capture_debug_info(struct debug_context *ctx)
{
struct task_struct *task = current;
memcpy(ctx->registers, task_pt_regs(task), sizeof(ctx->registers));
ctx->regs = task_pt_regs(task);
ctx->ip = instruction_pointer(ctx->regs);
ctx->sp = kernel_stack_pointer(ctx->regs);
ctx->cpu = smp_processor_id();
ctx->pid = task->pid;
memcpy(ctx->comm, task->comm, TASK_COMM_LEN);
}
Stack Trace Analysis Implementation
The stack_frame structure represents a single frame in the stack trace. The analyze_stack_trace function walks the stack and captures the return addresses of each frame.
struct stack_frame {
struct stack_frame *next_frame;
unsigned long return_address;
};
static void analyze_stack_trace(struct debug_context *ctx)
{
struct stack_frame *frame = (struct stack_frame *)ctx->sp;
unsigned int depth = 0;
unsigned long flags;
spin_lock_irqsave(&debugger.debug_lock, flags);
while (!kstack_end(frame) && depth < MAX_STACK_TRACE_DEPTH) {
if (!validate_stack_ptr(frame)) {
break;
}
debugger.stack_trace[depth++] = frame->return_address;
frame = frame->next_frame;
}
debugger.trace_size = depth;
spin_unlock_irqrestore(&debugger.debug_lock, flags);
}
The print_stack_trace function prints the captured stack trace to the kernel log.
static void print_stack_trace(void)
{
char symbol[KSYM_SYMBOL_LEN];
unsigned int i;
for (i = 0; i < debugger.trace_size; i++) {
sprint_symbol(symbol, debugger.stack_trace[i]);
printk(KERN_INFO "[<%pK>] %s\n",
(void *)debugger.stack_trace[i],
symbol);
}
}
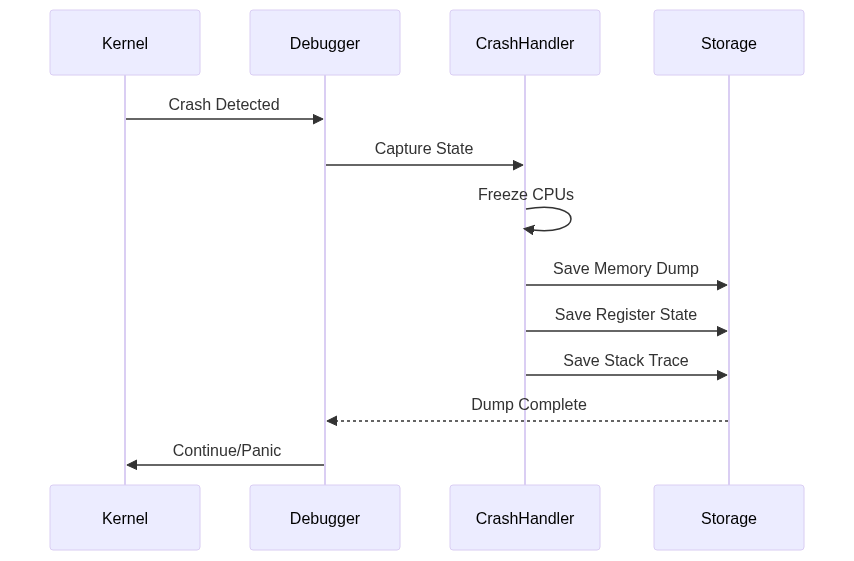
Crash Dump Collection
The crash dump collection process is illustrated using a sequence diagram. The diagram shows the interaction between the kernel, debugger, crash handler, and storage.
Memory Analysis Implementation
The memory_region structure represents a region of memory. The analyze_memory_region function captures the contents of a memory region and stores it in the crash dump buffer.
struct memory_region {
unsigned long start;
unsigned long end;
unsigned int flags;
char description[64];
};
static int analyze_memory_region(struct memory_region *region,
void *buffer,
size_t size)
{
struct page *page;
void *vaddr;
int ret = 0;
if (!pfn_valid(__pa(region->start) >> PAGE_SHIFT))
return -EINVAL;
page = virt_to_page(region->start);
vaddr = page_address(page);
if (vaddr && size <= PAGE_SIZE) {
memcpy(buffer, vaddr, size);
ret = size;
}
return ret;
}
The dump_memory_info function iterates over the memory regions of the current process and captures their contents.
static void dump_memory_info(struct debug_context *ctx)
{
struct mm_struct *mm = current->mm;
struct vm_area_struct *vma;
unsigned long flags;
if (!mm)
return;
down_read(&mm->mmap_sem);
for (vma = mm->mmap; vma; vma = vma->vm_next) {
struct memory_region region = {
.start = vma->vm_start,
.end = vma->vm_end,
.flags = vma->vm_flags,
};
snprintf(region.description, sizeof(region.description),
"VMA %lx-%lx %c%c%c",
region.start, region.end,
(region.flags & VM_READ) ? 'r' : '-',
(region.flags & VM_WRITE) ? 'w' : '-',
(region.flags & VM_EXEC) ? 'x' : '-');
analyze_memory_region(®ion, debugger.crash_buffer,
MIN(region.end - region.start,
MAX_CRASH_DUMP_SIZE));
}
up_read(&mm->mmap_sem);
}
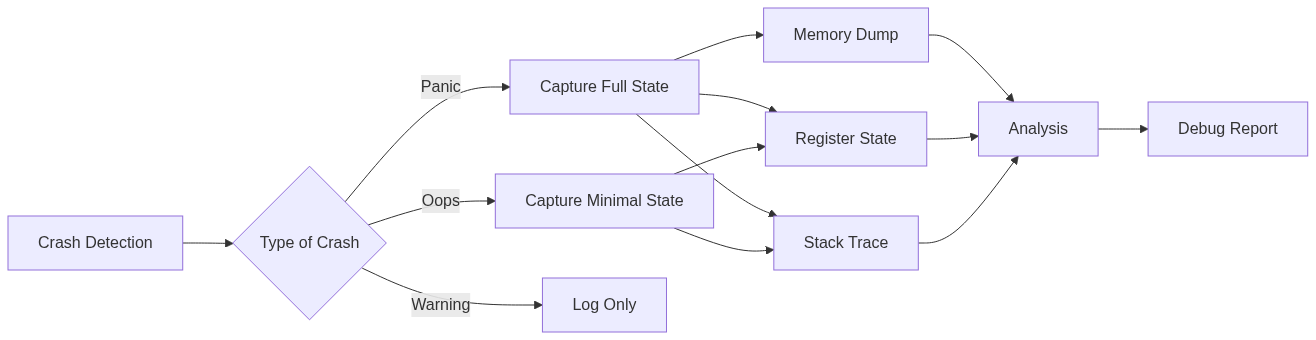
Debug Flow
The below graph shows the steps involved in crash detection, state capture, and analysis.
Live Debugging Features
The breakpoint structure represents a breakpoint. The set_breakpoint function sets a breakpoint at a specified address and installs a handler.
struct breakpoint {
unsigned long address;
unsigned long original_instruction;
bool enabled;
void (*handler)(struct pt_regs *);
};
static int set_breakpoint(struct breakpoint *bp,
unsigned long addr,
void (*handler)(struct pt_regs *))
{
unsigned long flags;
if (!kernel_text_address(addr))
return -EINVAL;
bp->address = addr;
bp->handler = handler;
local_irq_save(flags);
probe_kernel_read(&bp->original_instruction,
(void *)addr,
BREAK_INSTR_SIZE);
probe_kernel_write((void *)addr,
BREAK_INSTR,
BREAK_INSTR_SIZE);
local_irq_restore(flags);
bp->enabled = true;
return 0;
}
Performance Monitoring
The debug_metrics structure tracks performance metrics, such as the number of breakpoint hits, stack traces captured, and memory dumps collected.
struct debug_metrics {
atomic64_t breakpoint_hits;
atomic64_t stack_traces_captured;
atomic64_t memory_dumps_collected;
atomic64_t total_debug_time_ns;
struct {
atomic_t count;
atomic64_t total_size;
} crash_dumps;
};
static struct debug_metrics metrics;
static void update_debug_metrics(unsigned long start_time)
{
unsigned long end_time = ktime_get_ns();
atomic64_add(end_time - start_time, &metrics.total_debug_time_ns);
}
Conclusion
Kernel debugging techniques require sophisticated implementations to effectively analyze and diagnose system issues. The provided implementation demonstrates practical approaches to building robust debugging tools for kernel development and maintenance. By following the principles and techniques discussed in this guide, you can design and implement kernel debugging tools that meet the demands of modern operating systems.