Day 68: From User to Kernel: Implementing Dynamic Syscall Handling for Robust Operating Systems”
Introduction
This article explores sophisticated implementations of dynamic syscall handling, focusing on runtime registration, parameter validation, and security measures. System calls are the primary interface between user-space applications and the kernel, making their efficient and secure handling essential for system stability and performance.
The implementation discussed here focuses on building a dynamic syscall system that allows syscalls to be registered and unregistered at runtime. This system includes robust parameter validation, security checks, and performance optimizations. By the end of this guide, you will have a solid understanding of how to design and implement advanced syscall handling mechanisms suitable for modern operating systems.
Syscall Architecture
The architecture of the dynamic syscall system is built around several core components. The first is dynamic registration, which allows syscalls to be added and removed at runtime. This is particularly useful for kernel modules that need to expose new functionality to user-space applications. The system supports both built-in and dynamically loaded syscalls, with proper reference counting to ensure that syscalls are not removed while in use.
Another key component is parameter handling, which involves validating and copying parameters between user and kernel space. The system implements secure data transfer with boundary checking to prevent buffer overflows and other security vulnerabilities. This ensures that syscalls can safely handle user-provided data.
Finally, the system includes a security context that performs comprehensive security checks and privilege management for syscall execution. This ensures that only authorized processes can execute privileged syscalls, reducing the risk of security breaches.
Implementation of Dynamic Syscall System
The implementation begins with defining the syscall_entry structure, which represents a single syscall. This structure includes the syscall number, handler function, number of arguments, and other metadata. The syscall_table structure manages the registry of syscalls, using a hash table for efficient lookup.
#include <linux/module.h>
#include <linux/kernel.h>
#include <linux/syscalls.h>
#include <linux/uaccess.h>
#include <linux/slab.h>
#include <linux/spinlock.h>
#include <linux/hash.h>
#include <linux/list.h>
#define MAX_SYSCALL_ARGS 6
#define SYSCALL_TABLE_SIZE 1024
struct syscall_entry {
unsigned long nr;
void *handler;
unsigned int num_args;
struct list_head list;
atomic_t ref_count;
bool is_dynamic;
char name[64];
};
struct syscall_table {
struct list_head *buckets;
spinlock_t lock;
unsigned int count;
unsigned int size;
};
struct syscall_context {
struct task_struct *task;
unsigned long args[MAX_SYSCALL_ARGS];
unsigned long syscall_nr;
void *user_data;
int result;
};
static struct syscall_table syscall_registry;
The init_syscall_registry function initializes the syscall registry. It allocates memory for the hash table, initializes the spinlock, and sets up the list heads for each bucket.
static int init_syscall_registry(void)
{
int i;
syscall_registry.buckets = kmalloc_array(SYSCALL_TABLE_SIZE,
sizeof(struct list_head),
GFP_KERNEL);
if (!syscall_registry.buckets)
return -ENOMEM;
for (i = 0; i < SYSCALL_TABLE_SIZE; i++)
INIT_LIST_HEAD(&syscall_registry.buckets[i]);
spin_lock_init(&syscall_registry.lock);
syscall_registry.count = 0;
syscall_registry.size = SYSCALL_TABLE_SIZE;
return 0;
}
The register_syscall function registers a new syscall. It allocates memory for the syscall entry, initializes its fields, and adds it to the appropriate bucket in the hash table.
static struct syscall_entry *register_syscall(unsigned long nr,
void *handler,
unsigned int num_args,
const char *name)
{
struct syscall_entry *entry;
unsigned long flags;
unsigned int hash;
entry = kmalloc(sizeof(*entry), GFP_KERNEL);
if (!entry)
return ERR_PTR(-ENOMEM);
entry->nr = nr;
entry->handler = handler;
entry->num_args = num_args;
entry->is_dynamic = true;
atomic_set(&entry->ref_count, 1);
strlcpy(entry->name, name, sizeof(entry->name));
hash = hash_long(nr, ilog2(SYSCALL_TABLE_SIZE));
spin_lock_irqsave(&syscall_registry.lock, flags);
list_add_rcu(&entry->list, &syscall_registry.buckets[hash]);
syscall_registry.count++;
spin_unlock_irqrestore(&syscall_registry.lock, flags);
return entry;
}
Parameter Validation and Copying
The param_validator structure defines the validation rules for a syscall parameter. The validate_syscall_params function validates the parameters of a syscall, ensuring that they fall within the specified bounds and are safe to use.
struct param_validator {
unsigned long min_value;
unsigned long max_value;
unsigned int flags;
int (*custom_validator)(const void *, size_t);
};
static int validate_syscall_params(struct syscall_context *ctx,
const struct param_validator *validators,
unsigned int num_params)
{
unsigned int i;
int ret = 0;
for (i = 0; i < num_params && i < MAX_SYSCALL_ARGS; i++) {
const struct param_validator *validator = &validators[i];
unsigned long param = ctx->args[i];
if (param < validator->min_value ||
param > validator->max_value)
return -EINVAL;
if (validator->flags & PARAM_FLAG_PTR) {
if (!access_ok((void *)param, sizeof(void *)))
return -EFAULT;
}
if (validator->custom_validator) {
ret = validator->custom_validator((void *)param,
sizeof(unsigned long));
if (ret < 0)
return ret;
}
}
return 0;
}
The copy_from_user_checked function safely copies data from user space to kernel space, ensuring that the source address is valid and the copy operation succeeds.
static int copy_from_user_checked(void *dst,
const void __user *src,
size_t size)
{
if (!access_ok(src, size))
return -EFAULT;
if (copy_from_user(dst, src, size))
return -EFAULT;
return 0;
}
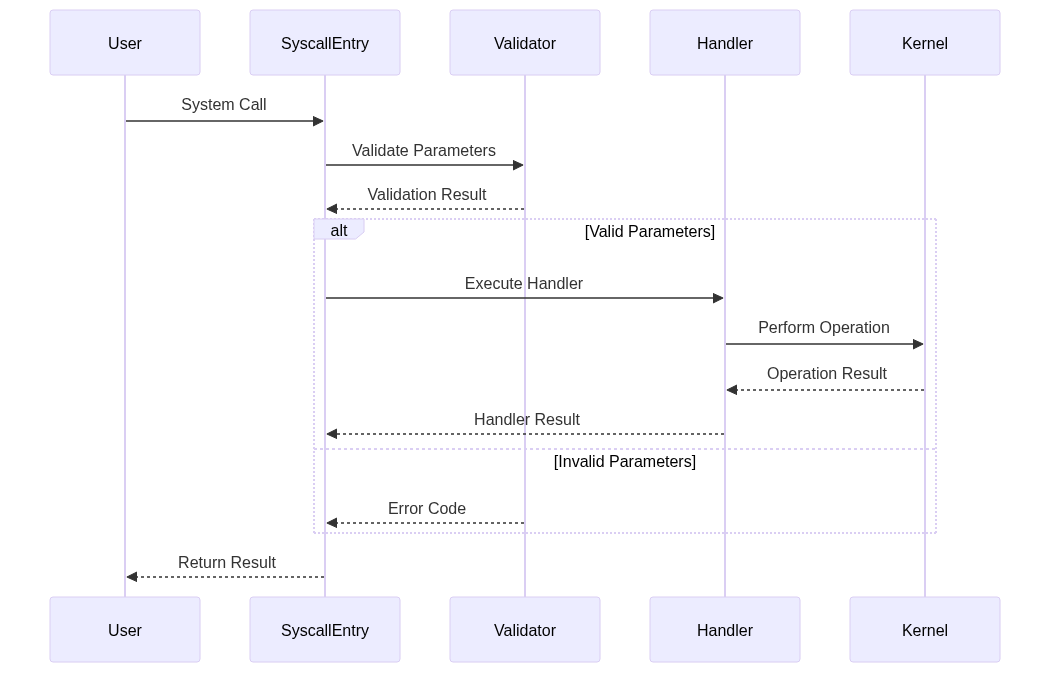
Syscall Flow Architecture
The syscall flow architecture is illustrated using a sequence diagram. The diagram shows the interaction between the user, syscall entry, validator, handler, and kernel.
Security Implementation
The syscall_security_context structure represents the security context of a syscall. The check_syscall_permissions function checks whether the current process has the necessary permissions to execute the syscall.
struct syscall_security_context {
kuid_t uid;
kgid_t gid;
kernel_cap_t caps;
unsigned long security_flags;
};
static int check_syscall_permissions(struct syscall_context *ctx,
unsigned long required_caps)
{
const struct cred *cred = current_cred();
struct syscall_security_context sec_ctx = {
.uid = cred->uid,
.gid = cred->gid,
.caps = cred->cap_effective,
};
if (!capable(CAP_SYS_ADMIN) &&
!ns_capable(current_user_ns(), CAP_SYS_ADMIN))
return -EPERM;
if ((required_caps & ~sec_ctx.caps.cap[0]) != 0)
return -EPERM;
return 0;
}
Performance Optimization
The syscall_cache structure represents a cache for syscall results. The init_syscall_cache function initializes the cache, and the update_syscall_stats function updates performance statistics.
struct syscall_cache {
struct lru_cache *cache;
spinlock_t lock;
unsigned int hits;
unsigned int misses;
};
static struct syscall_cache *init_syscall_cache(void)
{
struct syscall_cache *cache;
cache = kmalloc(sizeof(*cache), GFP_KERNEL);
if (!cache)
return NULL;
cache->cache = kmalloc(sizeof(struct lru_cache), GFP_KERNEL);
if (!cache->cache) {
kfree(cache);
return NULL;
}
spin_lock_init(&cache->lock);
cache->hits = 0;
cache->misses = 0;
return cache;
}
static inline void update_syscall_stats(struct syscall_context *ctx,
unsigned long start_time)
{
unsigned long end_time = ktime_get_ns();
atomic64_add(end_time - start_time,
&ctx->task->syscall_stats.total_time);
atomic_inc(&ctx->task->syscall_stats.count);
}
Error Handling and Recovery
The syscall_error structure represents an error that occurred during syscall execution. The handle_syscall_error function handles the error, optionally retrying the syscall or logging the error.
struct syscall_error {
int error_code;
const char *message;
unsigned long flags;
void (*handler)(struct syscall_context *);
};
static void handle_syscall_error(struct syscall_context *ctx,
struct syscall_error *error)
{
if (error->flags & ERROR_FLAG_FATAL) {
printk(KERN_ERR "Fatal syscall error: %s\n", error->message);
if (error->handler)
error->handler(ctx);
}
ctx->result = error->error_code;
if (error->flags & ERROR_FLAG_RETRY)
schedule_delayed_work(&ctx->task->syscall_retry_work,
RETRY_DELAY);
}
Monitoring System
The syscall_monitor structure tracks syscall statistics, such as the total number of calls and errors. The update_monitor_stats function updates these statistics.
struct syscall_monitor {
atomic64_t total_calls;
atomic64_t total_errors;
struct {
atomic_t count;
atomic64_t total_time;
atomic_t error_count;
} syscalls[MAX_SYSCALL_NR];
};
static struct syscall_monitor *monitor;
static void update_monitor_stats(struct syscall_context *ctx,
int result,
unsigned long execution_time)
{
atomic64_inc(&monitor->total_calls);
if (result < 0)
atomic64_inc(&monitor->total_errors);
atomic_inc(&monitor->syscalls[ctx->syscall_nr].count);
atomic64_add(execution_time,
&monitor->syscalls[ctx->syscall_nr].total_time);
}
Conclusion
Advanced syscall handling requires careful attention to security, performance, and reliability. The provided implementation demonstrates practical approaches to building a robust syscall system suitable for modern operating systems. By following the principles and techniques discussed in this guide, you can design and implement advanced syscall handling mechanisms that meet the demands of modern operating systems.